You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Indian Special Forces (18 Viewers)
- Thread starter haldilal
- Start date
More options
Who Replied?- Joined
- Aug 24, 2024
- Messages
- 856
- Likes
- 2,130
Ye 7 walo ko ho kya gaya hai. 2 hafte se photos hi photos
- Joined
- Jul 5, 2024
- Messages
- 695
- Likes
- 2,706
i aint complaining lmaoYe 7 walo ko ho kya gaya hai. 2 hafte se photos hi photos
- Joined
- Jun 30, 2024
- Messages
- 203
- Likes
- 1,442
- Joined
- Jul 5, 2024
- Messages
- 695
- Likes
- 2,706
i swear i love the royal marine rifle the most... can someone run down the attachments and total cost on it
View: https://www.reddit.com/r/MilitaryPorn/comments/1ij1qxa/royal_marines_commando_armed_with_knights/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button
View: https://www.reddit.com/r/MilitaryPorn/comments/1ij1qxa/royal_marines_commando_armed_with_knights/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button
Last edited:
- Joined
- Jul 8, 2024
- Messages
- 220
- Likes
- 890
knights armament ks1 (l403a1), mcq-prt supperessor, vortex optics razor gen3 (i believe) lpvo+aimpoint acro red dot. £10,000- 11,000 i.e. $12-13,000.
- Joined
- Jul 8, 2024
- Messages
- 220
- Likes
- 890
i swear i love the royal marine rifle the most... can someone run down the attachments and total cost on it
View: https://www.reddit.com/r/MilitaryPorn/comments/1ij1qxa/royal_marines_commando_armed_with_knights/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button
- Joined
- Jul 4, 2024
- Messages
- 2,689
- Likes
- 13,554
i swear i love the royal marine rifle the most... can someone run down the attachments and total cost on it
View: https://www.reddit.com/r/MilitaryPorn/comments/1ij1qxa/royal_marines_commando_armed_with_knights/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button

Military - Knight's Armament
Vortex Eleanor

5.56 QDC/CRS-PRT - Knight's Armament Company- Suppressor
5.56 QDC/CRS-PRT - Knight's Armament Company- Suppressor-FDE

VooDoo-S
Overview VooDoo-S Short/Medium Range Multi-Mission Thermal Sight This item is a special order item. Please contact us for a current lead time. VooDoo-S is the next generation of tactical thermal imaging. We've kept what you require, improved what you've asked for, and added what you've always...
www.thirdcoastthermal.com
View: https://youtu.be/Ee8LvSwDSEY?si=8LPIje8eZ440LRmG
Last edited:
- Joined
- Jul 4, 2024
- Messages
- 2,689
- Likes
- 13,554
What are the advantages of having the optics so far away…almost seeing them regularly in Indian Army.
- Joined
- Jul 1, 2024
- Messages
- 1,014
- Likes
- 7,698
Our SFs need to be very very careful about what they procure.
View: https://x.com/aadilbrar/status/1886585557247283385?s=46
Hmmm, I am extremely sceptical about this news. I have an technical background and I have worked with drones.
This seems like an hitjob news on our desi drones, inserting relevant keywords (chinese, hacking) to spread panic and fear. I think some dumbo journalist is intentionally / unintentionally spreading misinformation and panic by classifying jamming with hacking.
If you envision that hacking a drone with Chinese tx/rx compoments will be as easy as starting up a laptop and typing some really scary commands really fast on a back-green screen, that's not how hacking works.
Hijacking has been done previously of much more complex dronesHmmm, I am extremely sceptical about this news. I have an technical background and I have worked with drones.
This seems like an hitjob news on our desi drones, inserting relevant keywords (chinese, hacking) to spread panic and fear. I think some dumbo journalist is intentionally / unintentionally spreading misinformation and panic by classifying jamming with hacking.
If you envision that hacking a drone with Chinese tx/rx compoments will be as easy as starting up a laptop and typing some really scary commands really fast on a back-green screen, that's not how hacking works.
If your tx/rx are compromised anything can happen. Remember bsnl huawei routers more than half decade back? Even secure corp laptops used to get injected with malware. Hijacking in military is not some nerd typing commands away on shell to glory - there are professional build solutions. And chinese have developed aplenty for drones spiked with their tx/rx components. Remember all those reserved space you read about in the tcp/ip etc packets in your Networking classes - that's where magic happens for some of the scenarios employed by US.
- Joined
- Jul 1, 2024
- Messages
- 1,014
- Likes
- 7,698
Hijacking has been done previously of much more complex drones
If your tx/rx are compromised anything can happen. Remember bsnl huawei routers more than half decade back? Even secure corp laptops used to get injected with malware. Hijacking in military is not some nerd typing commands away on shell to glory - there are professional build solutions.
Read the article yourself.
What they did -
- First they cut off communications links (Basically jammed the comm. using high-powered jammers).
- Then reconfigured the drone’s GPS coordinates to make it land at what the drone thought was its actual home base – but instead was in Iran. (Basically GPS jamming + spoofing the GPS signals to seem like the home base was Iran).
From IdeaForge SWITCH's brouchure -
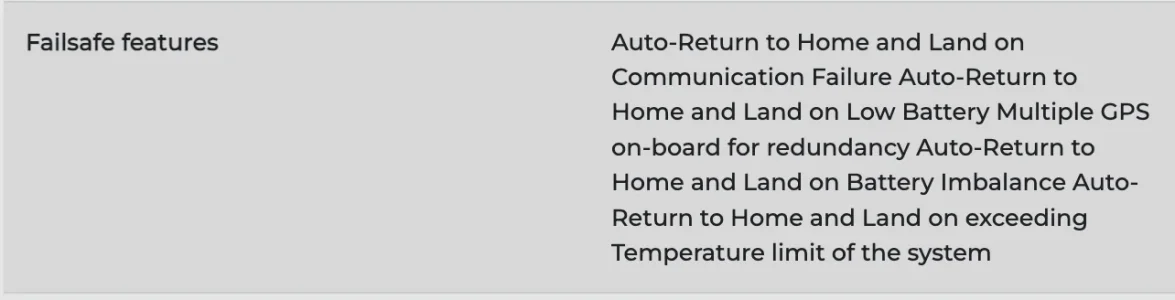
So basically if comm. failure happens it will automatically try to return to base. But how it will figure out where is the base ? Using GPS coordinates, which, again can be spoofed just as mentioned above.
Nothing to do with Chinese components.
And chinese have developed aplenty for drones spiked with their tx/rx components. Remember all those reserved space you read about in the tcp/ip etc packets in your Networking classes - that's where magic happens for some of the scenarios employed by US.
Drone Tx/Rx comm. don't use TCP/IP protocol just an FYI. Also this -
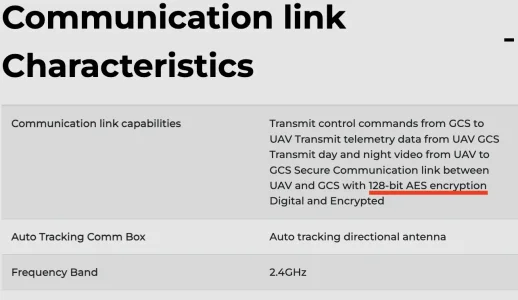
What the para and the underlined red means, is that regardless of whatever Tx/Rx backdoors Chinese can create, the original comm. & commands are securely encrypted and cannot be intercepted or spoofed.
Its like, lets say you are sending a postcard to your friend, and your mailman is Chinese. So you write the postcard in your own secret code which only you and your friend know. So no matter how hard the postman tries to read or decipher it, he can't.
- Joined
- Jun 30, 2024
- Messages
- 951
- Likes
- 3,989
i swear i love the royal marine rifle the most... can someone run down the attachments and total cost on it
View: https://www.reddit.com/r/MilitaryPorn/comments/1ij1qxa/royal_marines_commando_armed_with_knights/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button
this is standard issue UKSF and Royal marines rifles
Jay Cal....ex 22 SAS on GBRS Group was one of the first to test it
View: https://www.youtube.com/shorts/yV5Aytbf8OY
- Joined
- Jun 30, 2024
- Messages
- 1,278
- Likes
- 5,212
Yup it was jammed but they wanted to add some masala so they called it hacking .Hmmm, I am extremely sceptical about this news. I have an technical background and I have worked with drones.
This seems like an hitjob news on our desi drones, inserting relevant keywords (chinese, hacking) to spread panic and fear. I think some dumbo journalist is intentionally / unintentionally spreading misinformation and panic by classifying jamming with hacking.
If you envision that hacking a drone with Chinese tx/rx compoments will be as easy as starting up a laptop and typing some really scary commands really fast on a back-green screen, that's not how hacking works.
- Joined
- Jul 4, 2024
- Messages
- 2,689
- Likes
- 13,554
View: https://youtube.com/shorts/zT2y168isKM?si=PZ3ylMbhr7PnLEUW

Defence Ministry to return Rs 12,500 crore unused funds amid procurement delays
The Centre allocated Rs 6,81,210 crore for the defence budget for 2025-26, up from last year's outlay of Rs 6,21,940 crore. However, the Defence Ministry is expected to return Rs 12,500 crore from its 2024-25 budget due to delays in the procurement process.
Cost of rifle -almost 10 lacs
Funds returned- 12500 crore
Size of Para SF ..approx 10,000
Do the maths!!
- Joined
- Jul 5, 2024
- Messages
- 2,183
- Likes
- 10,822
- Joined
- Jul 8, 2024
- Messages
- 220
- Likes
- 890
this is standard issue UKSF and Royal marines rifles
Jay Cal....ex 22 SAS on GBRS Group was one of the first to test it
View: https://www.youtube.com/shorts/yV5Aytbf8OY
Dont think its the standard issue. Sort of like how m4 works for para sf. Just another option for operators
- Joined
- Aug 24, 2024
- Messages
- 856
- Likes
- 2,130
Help me understand this - a very naive proposition coming from a noob:
View: https://youtube.com/playlist?list=PLOv4gE-dhrTA6JXOaIuRJOWacAI_taHf8&si=t6pAIdk5vQrfgMBL
What if a Para captain/major watches this and tries to implement it in his own unit?
Will his ustaads/seniors let him? Or make fun/dismiss it altogether saying lol, internet se sikhake hume sikhayenge!
From a novice POV, I think they have a chance of improving their CQB by 15-20% if they learn wholeheartedly from this.
No dissing/satire on this one plz - looking for a reasonable answer to a genuine query.
@Airborne22 @Arad Operator @Baseplate @Noob (+ folks who've seen how units function upclose)
View: https://youtube.com/playlist?list=PLOv4gE-dhrTA6JXOaIuRJOWacAI_taHf8&si=t6pAIdk5vQrfgMBL
What if a Para captain/major watches this and tries to implement it in his own unit?
Will his ustaads/seniors let him? Or make fun/dismiss it altogether saying lol, internet se sikhake hume sikhayenge!
From a novice POV, I think they have a chance of improving their CQB by 15-20% if they learn wholeheartedly from this.
No dissing/satire on this one plz - looking for a reasonable answer to a genuine query.
@Airborne22 @Arad Operator @Baseplate @Noob (+ folks who've seen how units function upclose)
- Joined
- Jul 4, 2024
- Messages
- 102
- Likes
- 264
Help me understand this - a very naive proposition coming from a noob:
View: https://youtube.com/playlist?list=PLOv4gE-dhrTA6JXOaIuRJOWacAI_taHf8&si=t6pAIdk5vQrfgMBL
What if a Para captain/major watches this and tries to implement it in his own unit?
Will his ustaads/seniors let him? Or make fun/dismiss it altogether saying lol, internet se sikhake hume sikhayenge!
From a novice POV, I think they have a chance of improving their CQB by 15-20% if they learn wholeheartedly from this.
No dissing/satire on this one plz - looking for a reasonable answer to a genuine query.
@Airborne22 @Arad Operator @Baseplate @Noob (+ folks who've seen how units function upclose)
I think it would depend on the senior. Not all of them would be closed to this or all of them open to this. I think a pretty big chunk of them would dismiss this saying "internet se sikhake hume sikhayenge". If that was not the case then with the amount of knowledge available on the net para sf guys would have already implemented a lot of these. IMO
Users who are viewing this thread
Total: 9 (members: 4, guests: 5)
Similar threads
- Replies
- 0
- Views
- 58
- Replies
- 6
- Views
- 386
Latest Replies
-
Indo-China Border & LAC
- Azaad
-
DRDO & PSUs
- Varoon4
-
Indian Air Force: News & Discussions
- Noob_Saibot
-
-
Russian Ukrainian War
- WW2historian
-
Indian Economy
- Azaad
-
Türkiye: News, Discussions & Updates.
- yasincsoy
-
Sinking State of Bangladesh: Idiotic Musings
- neelaslayer






